Security Brain SIEM
Product
Security Brain Security Information and Event Management (Security Brain SIEM)
Overview
Security Brain SIEM is an open unified platform which deploys core capabilities of 360 Cloud Security Brain locally for analytics, triage, alerting, response, and assessment based on cloud computing, big data, artificial intelligence and other new-generation information technologies. The platform, modularized and combined to form a multi-scenario solution, can visualize, automate, and intelligently complete security operations such as situational awareness, advanced threat detection, automatic threat response, and defense capability assessment.
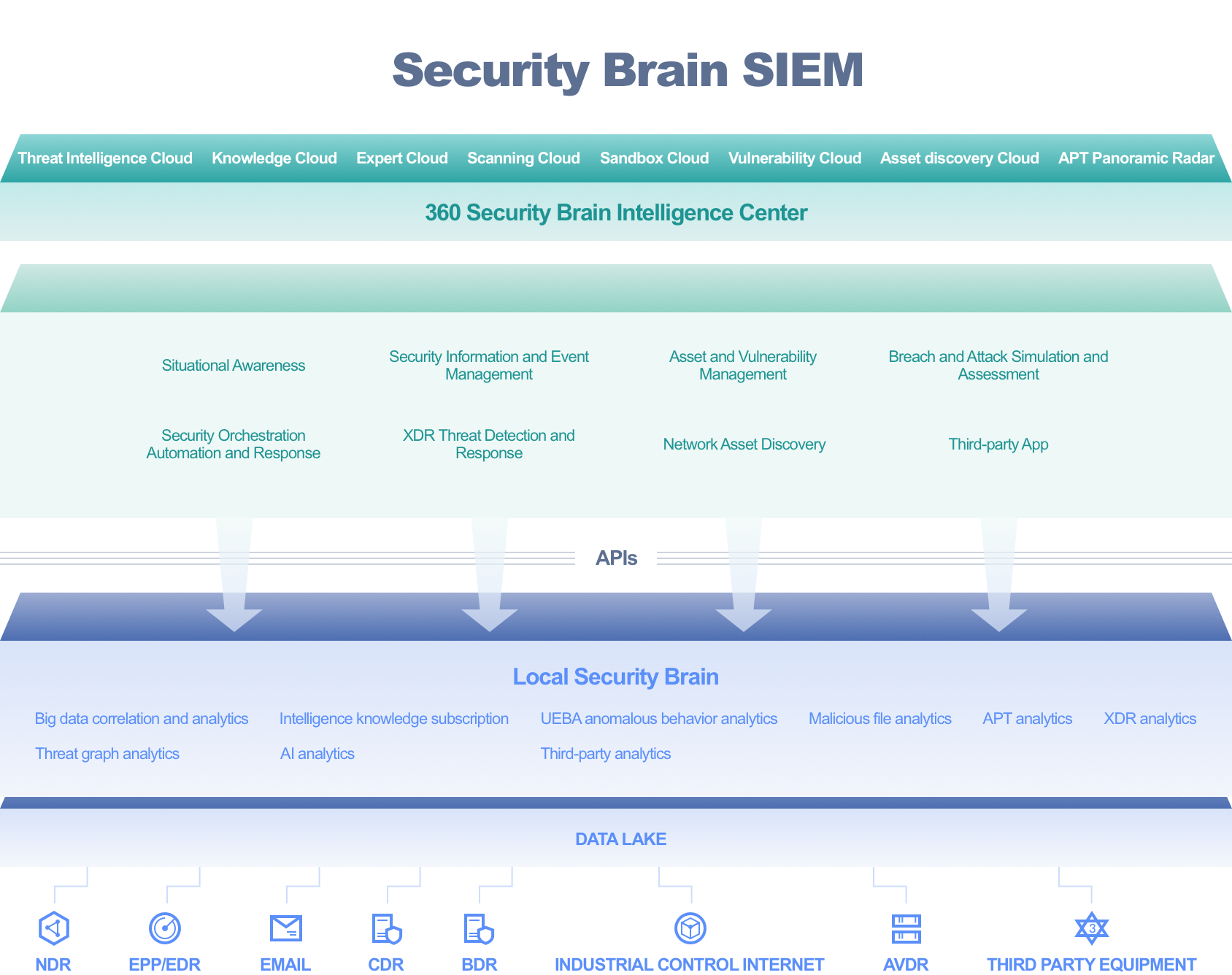
Features
Empowered by the Cloud Security Brain
360 Security Big Data collected 29 billion malicious files, 22 trillion security logs, 9 billion domain information, and more than 2 EB of security big data. After security experts analyze and research the data, 360 Security Big Data outputs security knowledge and threat maps to the local Security Brain platform. By using those data with multiple threat analytics engines of the local Security Brain platform, you will find many security problems that cannot be found by traditional methods.
Multi-dimensional Neuron, Full-view Analytics
The multi-dimensional neuron matrix is a set of professional perceptron networks trained by 360 company in long-term offensive and defensive drills, including multi-dimensional detection and response products such as endpoint, network, cloud, and mobile, which can gather the clues from all aspects of threat attacks on the local Security Brain platform. Security personnel can then analyze and deal with malicious attacks from a full perspective.
Multi-stage Noise Reduction, Precise Alerting
The analytics module of the local Security Brain platform controls the entire alert generation process in multiple stages, gradually improving the alert precision through self-circulation and self-learning. In the data aggregation stage, invalid alerts are removed and similar alerts are merged to reduce the number and noise of alerts. In the analysis stage, the 360 full-technology stack intelligent detection and analytics engine identifies high-risk incidents from massive alerts, and removes false positives through cross-validation. During security operations, the data processing process, event analytics rules and aggregation model are constantly optimized, and a positive feedback loop is used to continuously improve the alert precision.
Automated Response Based on Expert Experience
360 security experts have summed up various types of security operations tactics based on years of practical offense-defense experience, which have been preset in the SOAR system and solidified into executable response playbooks. Customers can adjust the configuration of playbooks in SOAR according to the actual situation to automate the execution of security operations processes such as threat detection, security analysis, and incident response, thus freeing security personnel from daily repetitive and heavy work, shortening the response MTTR, and improving the efficiency and effectiveness of security operations.
Automated Attack Simulation and Assessment
Actions speak louder than words. If security personnel have no real offense-defense combat experience, it will be difficult for them to develop practical security operation capabilities. Breach and Attack Simulation (BAS) uses the attack simulation technology as well as a real offense-defense panorama knowledge base to systematically assess security defense capabilities with the ATT&CK attack technology framework and promote system protection and security construction with real combat simulation methods. BAS provides different assess solutions for perimeter, intranet, Email, endpoint, and data protection, and users can freely choose according to their needs. After attack agents and targets are set up, BAS can automatically run on a regular basis to assess and test the real protection level of a customer by using the latest attack methods and the data synchronized from the cloud side, and finally generate analysis reports and reinforcement recommendations for security teams to improve their systems.
Hierarchical Deployment, Global Analysis
The local Security Brain platform analyzes and processes mass data using big data technology. It supports the hierarchical deployment mode, which means that the headquarters and subordinate branches can be deployed hierarchically according to the needs of customers. The headquarters can monitor and check the security situation and alerts of each branch, directly retrieve or trace and analyze the source log information of each branch, and use global rules to achieve unified correlation analysis between the headquarters and each branch. In this way, the platform implements hierarchical deployment, data synchronization, and global unified analysis.
Expert Service, Collaborative Defense
Security operations are inseparable from not only data, tools, and processes, but also security professionals. 360 company has a team of over 3,800 security experts, 14 teams of offense-defense experts, and 10 security research centers. The company has accumulated rich experience in offense-defense combats. Security experts of 360 company can assist customers in the analysis, research, and response of security incidents, reducing risks for customer security teams and improving the efficiency and effectiveness of security operations.
Highlights
August 2022, recognized again in Forrester Security Analytics Platform report, The Security Analytics Platform Landscape, Q3 2022
August 2020, the only China-based vendor recognized in the Forrester Security Analytics Platform annual report Now Tech: Security Analytics Platforms, Q3 2020
July 2020, the only China-based vendor recognized in the 2020 Gartner Peer Insights ‘Voice of Customer’: Security Information and Event Management report
February 2020, the only China-based vendor recognized in the 2020 Gartner Magic Quadrant for Security Information and Event Management report
May 2019, the only China-based vendor recognized in the 2019 Gartner Peer Insights ‘Voice of Customer’: Security Information and Event Management report
December 2018, mentioned in the 2018 Gartner Magic Quadrant for Security Information and Event Management report


