360 Endpoint Detection Response (EDR) System
360 EDR is a new type of terminal security product that focuses on intrusion detection and response, and effectively responds to various advanced threats. Terminal process, network, file, driver, and other system behavior logs, using threat intelligence, various detection engines and
full attack link behavior analysis and other technical means on the server side to achieve accurate detection of advanced threats, automatic alarm correlation, Visual display of attack links, efficient source traceability, intrusion event response and blocking, etc. At the same time, it supports flexible retrieval of terminal massive behavior logs, threat hunting, and fully utilize the big data storage and processing capabilities of the core security brain and threat intelligence on the Cloud.
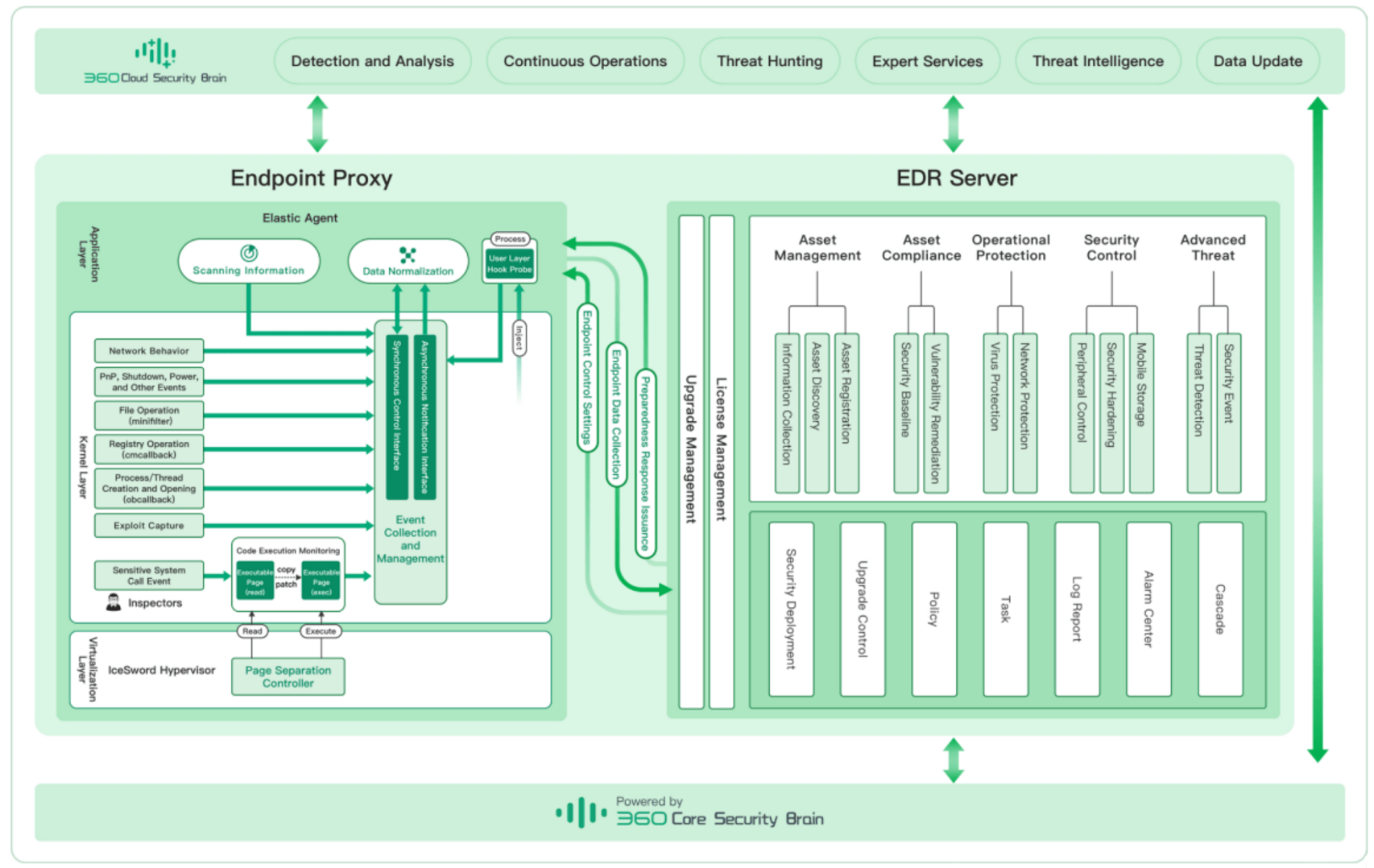
The core technical architecture of 360 EDR consists of three parts: including the terminal probe Agent, EDR Server, and the core security brain module, of which the terminal probe Agent is the core component of 360 EDR. The core crystal engine and the comprehensive monitoring technology under the kernel layer realize the whole process, allround, high-quality data collection during the attack process, abstract and normalize it and transfer it to the EDR Server for threat retrieval, and accept and process the EDR Server at the same time. The disposal command to the terminal can control the threat in time. EDR Server can manage terminals, and add security management services to basic capabilities such as upgrades, tasks, and policies, including asset management, operation protection, and security control. To the advanced threat, through its built-in threat analysis engine, combined with threat intelligence, it realizes threat detection, and provides rich threat suppression capabilities. Terminal threats can be handled manually or automatically to minimize the impact of threats. 360 Core Security Brain, as an underlying module, brings common functions and components to provide EDR Server with the basic support required for threat detection operations, including big data storage and graph databases. When connecting to the Internet, EDR products will cooperate with the 360 cloud security brain, which can make full use of the whole network big data for security event correlation analysis, realize continuous operation of threat intelligence, and effectively using security expert services.
The core technical architecture of 360 EDR consists of three parts: including the terminal probe Agent, EDR Server, and the core security brain module, of which the terminal probe Agent is the core component of 360 EDR. The core crystal engine and the comprehensive monitoring technology under the kernel layer realize the whole process, allround, high-quality data collection during the attack process, abstract and normalize it and transfer it to the EDR Server for threat retrieval, and accept and process the EDR Server at the same time. The disposal command to the terminal can control the threat in time. EDR Server can manage terminals, and add security management services to basic capabilities such as upgrades, tasks, and policies, including asset management, operation protection, and security control. To the advanced threat, through its built-in threat analysis engine, combined with threat intelligence, it realizes threat detection, and provides rich threat suppression capabilities. Terminal threats can be handled manually or automatically to minimize the impact of threats. 360 Core Security Brain, as an underlying module, brings common functions and components to provide EDR Server with the basic support required for threat detection operations, including big data storage and graph databases. When connecting to the Internet, EDR products will cooperate with the 360 cloud security brain, which can make full use of the whole network big data for security event correlation analysis, realize continuous operation of threat intelligence, and effectively using security expert services.
Product Advantages:
360 Endpoint Detection Response (EDR) System is a future-oriented EDR product with SaaS-based and intelligent. Based on threat intelligence, it performs in-depth detection, intelligent analysis, and specialized processing of threat risks through continuous monitoring of endpoint activity behaviors with the support of 360 core security brain’s security big data, AI analysis, attack traceability and other powerful capabilities. Through SaaS-based technology solutions, it can significantly reduce user costs, improve deployment efficiency, and utilize the big data across the whole network to resolve endpoint security problems for users on all fronts.
As a future-oriented endpoint security product, 360 EDR has prominent advantages in terms of product implementation as follows:
As a future-oriented endpoint security product, 360 EDR has prominent advantages in terms of product implementation as follows:
High-quality data collection capability
High-quality data collection capability—the quality of endpoint data: The quality of data collected determines the true detection effect of EDR. It is often neglected and misunderstood that data collection is simple; while in fact, the collection of high-quality security data is one of the most challenging work in endpoint security. High-quality data—the dimensionality of data collected is the most important. Only multidimensional big data are the real big data, which include data before, during, and after the attack in terms of time; standard, differential, and sabotaging behaviors in terms of behavior; before, during, after infection in terms of phase, etc. Only such big data are high-quality data collected by EDR; only based on high-quality data can the
detection effect of EDR be truly exerted.
High-quality data—the accuracy of data collected is the second important. 360 core crystal engine directly captures the behavior of kernel vulnerability exploitation, which is far more efficient and accurate than speculating whether there is privilege escalation behavior by manually sieving through massive processes, file registry, and other data that are not directly related for clues. More importantly, current EDR products often adopt the approach of a few system standard interfaces (such as file registry and process callback mechanism), rely on Microsoft’s ETW(Event Tracing for Windows) provider, and inject HOOK into the application layer for large amounts of information that does not meet the requirements. These collection methods have the following problems: Firstly, they can be easily bypassed by attackers (e.g., Patching the patch, Direct system calls, P/Invoke to D/Invoke, Patching the Entrypoint, and other public attacks). Secondly, the data details cannot meet the high-precision requirements (e.g.: the RPC event data details of ETW are insufficient, while 360 EDR can record more complete and accurate parameter information through the RPC state tracking at the kernel level). 360 EDR uses the kernel analysis technology accumulated for over a decade, the unique and core crystal engine base on hardware virtualization, and multiple other engines to collect security data; that is, collect high-precision data based on topnotch endpoint technology capabilities.
360 EDR provides monitoring capabilities far beyond the kernel level, enhances the security protection of 64-bit systems by using the hardware virtualization mechanism of the CPU, and conducts comprehensive monitoring of process creation, process injection, module loading, register table modifying, file writing, etc. It avoids the drawbacks that traditional EDR relies heavily on Ring3 user-level monitoring technology, and can directly detect kernel and application layer 0-day exploits, effectively countering APT bypass attacks.
High-quality data—the accuracy of data collected is the second important. 360 core crystal engine directly captures the behavior of kernel vulnerability exploitation, which is far more efficient and accurate than speculating whether there is privilege escalation behavior by manually sieving through massive processes, file registry, and other data that are not directly related for clues. More importantly, current EDR products often adopt the approach of a few system standard interfaces (such as file registry and process callback mechanism), rely on Microsoft’s ETW(Event Tracing for Windows) provider, and inject HOOK into the application layer for large amounts of information that does not meet the requirements. These collection methods have the following problems: Firstly, they can be easily bypassed by attackers (e.g., Patching the patch, Direct system calls, P/Invoke to D/Invoke, Patching the Entrypoint, and other public attacks). Secondly, the data details cannot meet the high-precision requirements (e.g.: the RPC event data details of ETW are insufficient, while 360 EDR can record more complete and accurate parameter information through the RPC state tracking at the kernel level). 360 EDR uses the kernel analysis technology accumulated for over a decade, the unique and core crystal engine base on hardware virtualization, and multiple other engines to collect security data; that is, collect high-precision data based on topnotch endpoint technology capabilities.
360 EDR provides monitoring capabilities far beyond the kernel level, enhances the security protection of 64-bit systems by using the hardware virtualization mechanism of the CPU, and conducts comprehensive monitoring of process creation, process injection, module loading, register table modifying, file writing, etc. It avoids the drawbacks that traditional EDR relies heavily on Ring3 user-level monitoring technology, and can directly detect kernel and application layer 0-day exploits, effectively countering APT bypass attacks.
Massive security big data
With big data as sustained driving force, 360 EDR implements real-time synchronization of global threats and continue to enhance the capabilities to detect and perceive APT attacks. Based on 17 years of practical experience, 360 has gathered more than 30 billion malicious samples, 22 trillion security logs, 8 billion domain name information, over 2EB of security big data, and can instantly call more than a million CPUs for the calculation, retrieval, and association of multidimensional threat data. This is the core advantage of 360 EDR, the highlighted strength of 360 multidimensional, high-quality security big data, which can quickly correlate security events across the entire network.
Security analysis capability
We believe that “seeing the threat” is a prerequisite for endpoint defense, and the level of threat detection capability directly affects the ability to “see”. 360 EDR analyzes massive multi-heterogeneous data through various detection and analysis technologies while combining network-wide APT intelligence to ensure comprehensive visibility of various threats. Visualization is the premise, without which any threat processing is a pipe dream. Threat visualization is the
“radar” capability of 360 EDR. This “radar” capability against all types of attacks requires strong security analysis capacity as guarantee. As a digital security leader with 17 years of history, 360 has built up a wealth of security capabilities from ToC to ToB/G, with the most powerful security analysis capabilities and technologies in China.
Professional team support capability
The human factor plays an essential role in the process of endpoint security confrontation. Based on a world-class team of security experts with years of counter attack and defense experiences, 360 EDR continuously hones the core functions of products and endows them with secure and effective detection and disposal capabilities. 360 has the strongest white hat legion in the eastern hemisphere with top vulnerability mining capabilities. So far, 360 experts have successfully mined over 3,000 CVE vulnerabilities from Google, Microsoft, Apple, and other mainstream vendors. It has received the top bug bounty in the history of Microsoft and Google, won the “Pwnie Awards”, the hacker community’s equivalent of The Oscars, and successfully
traced up to 50 overseas APT organizations against China, such as Ocean Lotus, HangOver, Mermaid, Bitter, and Sapphire Mushroom. These data suffice to prove 360’s professionalism and team capacity in counter-attack and defense, for which 360’s personnel with professional competency are indispensable, who are also the members of the expert team that has effectively improved various capability indicators of 360 EDR during its development.
Product deployment:
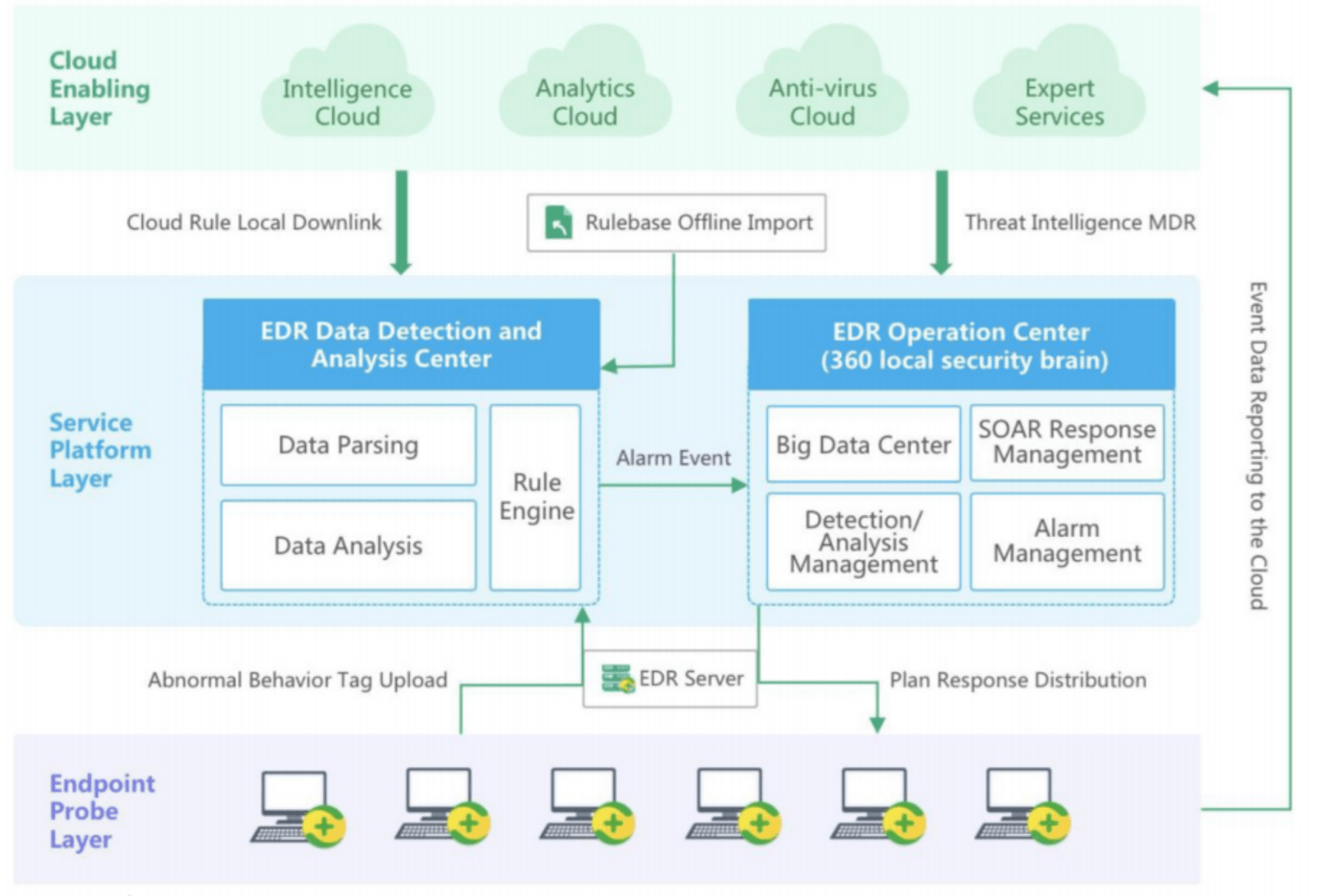
360 EDR provides two modes, cloud SaaSbased and local private deployment, to meet the security protection demand of both Internet and isolated network scenarios. SaaS-based EDR built on the 360 core security brain concept and security operation capability framework and the security protection system established from the cloud perspective enable extensive data linkage between various security events at the endpoint and big data in the cloud to implement an orderly evolution of security capabilities from siloed, passive single-point protection to active, global defense in depth. This network-based SaaS cloud security system protection is also the most effective protection way of EDR in the future, with inherent advantages of low cost and high
efficiency, greatly enhancing advanced threat event detection and traceability. Moreover, this capability is sustained, continuous, and able to self-correct and iterate quickly. For isolated network endpoint security defense scenarios, 360 EDR also provides a local private deployment mechanism that can endow the local network with cloud capabilities to implement a self-operating EDR management model.
Value of Next-Generation EDR Solutions:
Detecting and investigating security events are two core capabilities of EDR. In this cyber
attack traceability case, 360 EDR completely recorded and restored the whole process of APT attack through comprehensive and accurate endpoint abnormal data collection, endpoint behavior alarm noise reduction, and threat intelligence correlation analysis collision. This has fully demonstrated the prominent advantages of 360 EDR in abnormal event collection and big data analysis and tracing and reflected its great value in coping with APT attacks in a practical environment.
Accurate capture of critical behaviors
Based on the memory-level monitoring technology, 360 EDR can comprehensively monitor processes, registries, files, and network behaviors, including process creation, process injection, module loading, registry value writing, key registry writing, new file creation, file writing, network access, domain name resolution, etc.; accurately capture Office vulnerability exploitation, fileless attack behaviors, clearly see each critical attack process, and directly block any privilege escalation and domain control vulnerability exploitation when triggered, to prevent the customer’s key data from being stolen. 360 EDR adopts the “all-seeing eye” endpoint detection technology, which avoids the technical defects of traditional EDR solutions such as ETW and API Hook. It does not miss key process behaviors and abnormal calls, and does not miss any clues
of APT on the terminal. Effectively It avoids the problems of incomplete detection and missing fragments of traditional EDR products.
Complete traceability for APT attack chain
360 EDR provides the capability of complete traceability for advanced APT attacks. By combining the collected abnormal events with 360 big data analysis capabilities, a complete attack chain is mapped through threat intelligence collision. Based on the visualized attack chain, security operators can conduct comprehensive detection and visual traceability for various attack scenarios such as brute-force cracking, vulnerability privilege escalation, and dynamic link library hijacking.
Professional security operation mechanism
A professional security operation team plays a vital role in the process of responding to emergency security events. By deploying 360 EDR products, Customer has successfully deployed 360’s security expert operation capabilities accumulated for years to develop the corresponding threat detection and response processes from security state overview, security event analysis, response disposal, evaluation and improvement, and other one-stop security workstations. 360 has the leading professional cybersecurity offense-defensive and operations teams in the industry. During the implementation of 360 EDR in Customer, 360 security operations experts keep expanding from information and network security to business security through in-depth business scenarios for the real world to continuously improve the security capabilities and create a digital security protection system with continuous iteration and capacity growth for customers.


